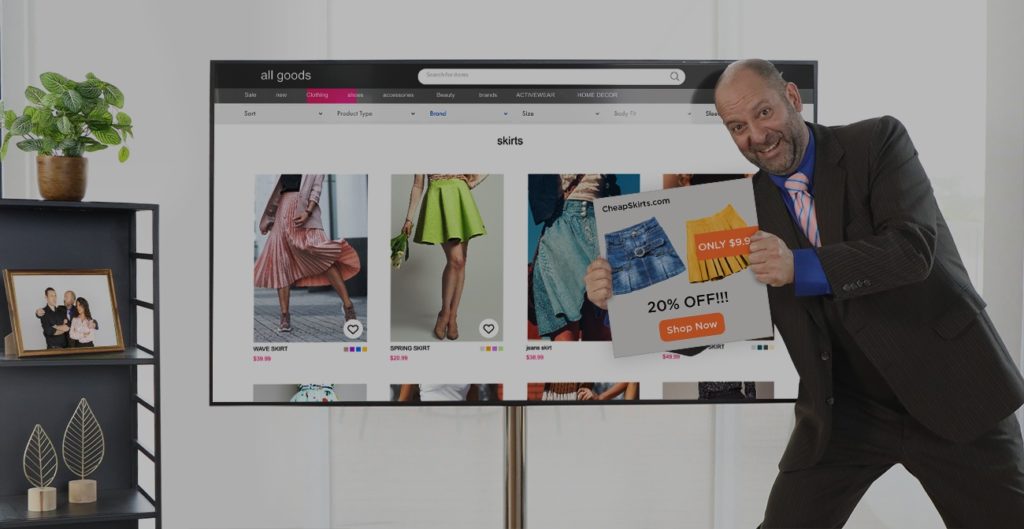
Your marketing team uses online ads as an essential tool for attracting the right visitors to the site. In fact, eMarketer projects that total digital ad spend in the U.S. will amount to $225.79 billion. But while your company relies on digital advertising to drive your traffic, there’s a large industry using the exact same method against you every day — ironically using your own website as their digital real estate. They’re traffic hijackers, and their entire revenue stream comes from placing unauthorized ads on retailers’ websites. This way, they profit off of your eCommerce traffic, all the while costing you in lost sales.
Simply put, traffic hijackers feed off your eCommerce visitors at your expense. They know how much money and resources brands like yours commit to attracting relevant shoppers to their websites. And these traffic hijackers know all they have to do to cash in is target this quality, ready-to-buy traffic and redirect it to other eCommerce offers.
How is this possible? It’s all about the under-the-radar methods traffic hijackers use to take advantage of a system that’s supposed to benefit companies like yours.
By the numbers: The payoff for traffic hijackers
Just how big of a bite are traffic hijackers taking from the eCommerce industry? Looking at U.S. online sales alone, our most conservative estimate reveals that traffic hijackers will generate $10.65 billion in sales this year. That’s because at a minimum, they succeed in shaving 1.5% off of retailers’ online sales revenue.
In just the second quarter of 2020, that revenue in the U.S. was over $200 billion — 44% more than the same period last year, according to the U.S. Census Bureau. And eMarketer projects that U.S. consumers will spend $710 billion in eCommerce this year.
Namogoo’s customer session data for over 250 online retail brands shows that 20% of all online shopping sessions are exposed to unauthorized ad injections year-round. While 1 out of every 5 visitors seeing competitor ads already presents a troubling issue for eCommerce retailers, understanding how these visitors become hijacked in the first place makes it clear why our customer journey data consistently shows that they are also the most valuable, converting at more than the double the rate of unaffected visitors.
By using our machine learning-based technology to stop traffic hijackers from disrupting their site visitors, clients across industries see their overall conversion rate increase between 1.5% and 5%.
These consistent and direct improvements as a result of preventing Customer Journey Hijacking spell out quite emphatically why traffic hijackers are so active and persistent: it’s become a multi-billion-dollar industry for them. And as eCommerce traffic continues to grow rapidly, so does the revenue being lost to Customer Journey Hijacking for retailers.
How traffic hijackers game the system
At its core, traffic hijackers’ approach is about exploiting the monetization tactics of ad networks, exchanges, and affiliates that are designed to help companies deliver the right advertisement to the right audience.
The way this system is supposed to work, ad networks buy their ad inventory from a wide variety of publishers and then place ads (at a charge) for businesses such as eCommerce companies.
Traffic hijackers manipulate this system by acting like publishers — except that the ad space these hijackers sell is essentially taken from eCommerce websites that they don’t own or partner with. This way, they effectively turn your website into online real estate promoting your competitors’ products — without your consent, and likely without your knowledge.
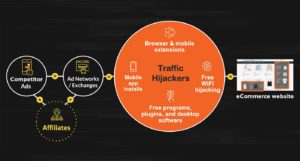
To pull this off, they need to reach your customers before they land on your eCommerce site — and they accomplish exactly that bundling their ad injections with the many free software services that consumers download every single day. This allows them to serve visitors on your site their ad inventory, and sell impressions and clicks to ad networks.
There are four main ways they do this:
- Developing and distributing supposedly legitimate (and in most cases free) software services that secretly include ad injectors. These services are then marketed as software that adds value to the consumer, such as desktop software (e.g. file converters, media players, and antivirus programs), browser extensions (e.g. deal and coupon notifications), and mobile apps (e.g. device performance boosters and games).
- Incentivizing other legitimate software services to bundle in their ad injectors via installation wizards in return for commission every time a user downloads and installs their software (pay-per-install).
- Misleading consumers into downloading popular, legitimate software through an alternative, unauthorized source that discreetly installs ad injectors along with the legitimate software.
- Taking advantage of free public Wi-Fi hotspots (for example, at cafes, hotels, airports, etc.) that monetize their services via ad injections.
How your traffic is fed competing ads without you knowing it
After a consumer downloads a service bundled with ad injections, traffic hijackers use a three-step process to deliver the most compelling ads at the most promising times in order to maximize their revenue. Here’s how it works:
- The ad injector tracks the consumer’s online browsing activity and builds a personal profile based on their preferences, habits, and other characteristics.
- When the consumer visits an eCommerce website, the ad injector automatically uses the personal profile it has developed to display targeted ads.
- When a consumer clicks on an injected ad, that ad leads them to a different website.
Since the injected ads themselves run entirely on the consumer’s browser or device, eCommerce site owners can’t see them at all, much less the way they impact the experience and behavior of these affected customers.
For good reason, traffic hijackers work hard to keep it this way. They constantly update their ad-injecting software and embed new services and extensions with injections to skim traffic undetected. And when one of their extensions from time to time is caught and taken down from the web store, they are refashioned and go live yet again under a different name.
The result: A customer experience that favors your competitors
Consumer-side ad injections are intended to entice the shopper to click, and many of them are designed to look like they’re actually part of the eCommerce website the consumer is visiting. They may include product ads, banners, and pop-ups, as in this example:
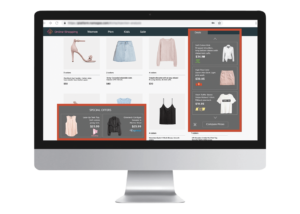
It’s also common for traffic hijackers to deceive consumers through discreet UI hijacking, so that a shopper who clicks on a link or button (e.g., sign in, add to cart, register, etc.) will be automatically redirected to an entirely different website. Here’s an example:

Our consumer session data shows that 60% to 65% of injected ads that appear to shoppers on eCommerce websites promote similar products sold by competing websites.
Turning the tables on traffic hijackers: the impact on your sales funnel
While consumer-side ad injections are a costly and widespread problem, retailers are not powerless against traffic hijackers. They can use Namogoo’s Customer Hijacking Prevention solution to automatically block ad injections in real time — essentially thwarting the handiwork of traffic hijackers and recovering online revenue that would have been funneled away. Online enterprises accomplishing this across several industries consistently see these KPIs pointing in the right direction:
- 1.5% to 5% uplift in overall conversion rate.
- 5% to 9% lower checkout abandonment rates.
- 5% to 7% higher revenue per visitor.
By taking back the customer journey they’ve invested in, eCommerce retailers can finally cut out traffic hijackers, and stop their eCommerce investments from leaking money.
Ready to stop traffic hijackers from profiting off of your eCommerce visitors at your expense? Request a demo today