As injected ads continue to affect online shoppers and the retailers they buy from, more of those retailers are becoming aware of what Customer Journey Hijacking (CJH) is and how it affects them. They are increasingly seeing that injected ads encourage many of their prospective customers to look for lower prices at competing online stores, while damaging their own customer relationships.
Some of these companies know that the most common method of CJH involves secretly infecting consumers’ digital devices with ad-injecting malware, which is often bundled with free software such as a browser extension or mobile app. And, if employees of these retailers have read our recent blog posts, they are likely to realize that users who shop online more actively are more prone to downloading these kinds of free software – which is why the most promising shoppers are disproportionately affected by CJH.
But there is another way unscrupulous third-parties can target shoppers with CJH, no matter how careful those shoppers are about the programs they download. Unfortunately, WiFi routers can sometimes offer hackers an alternative route to CJH, enabling them to hurt both your user experience and your sales numbers without requiring a shopper to actually install any software.
How does it work?
Here are the steps that typically occur when ad injectors leverage WiFi routers:
- Malicious code opens a router to attack: While consumer-grade routers could be penetrated by a resilient cyberattack, in most cases such a sophisticated attack isn’t even necessary. More often, a user unwittingly downloads malicious code that runs in the background on their browser. Then, when this user connects to a WiFi router, their malware infects the router and opens it to intrusion.
- Hacker conducts brute force attack on the router: Hackers or malicious actors commonly use a brute force attack on the infected router’s internal IP. This, the simplest method of attack, involves repeatedly entering various combinations of usernames and passwords (usually using automated software) until the software guesses the right password. While a person would take hours or even days to guess the correct password, a brute force attack can do it in seconds, trying tens of thousands of password variations or more until they break through a site or server with the correct password.
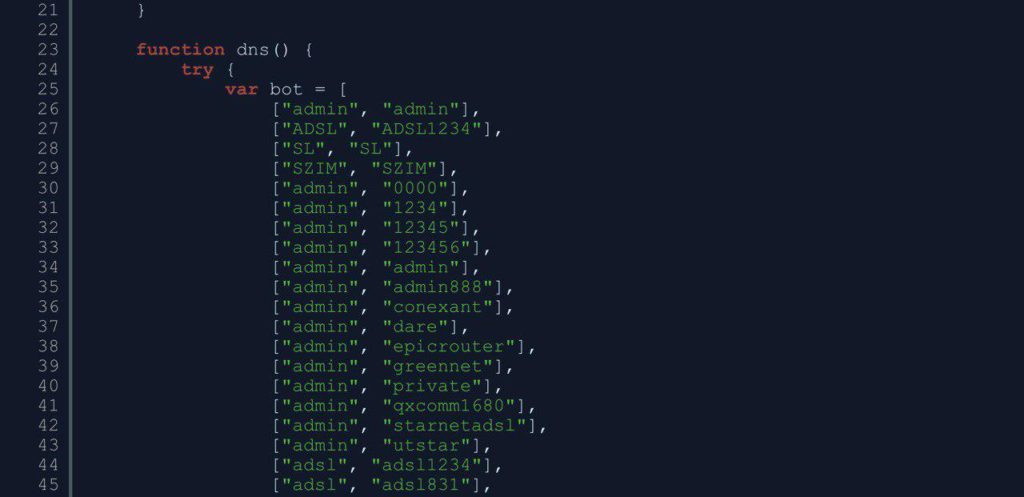
A brute force attack detected by Namogoo’s Code Insights Tool
- A proxy is created to reroute web traffic: Once the router’s admin password is cracked, hackers can essentially take control of the router’s admin console. They can then set up a proxy to redirect network traffic to a malicious IP address.
- Hackers activate the proxy: To activate the proxy, hackers force a reboot of the router.
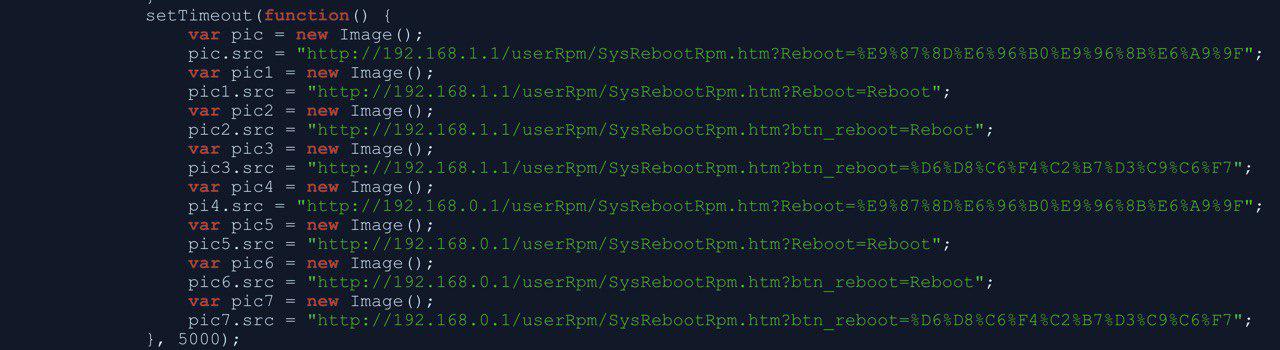
A WiFi router reboot script captured by Namogoo’s Code Insights Tool
- Hackers redirect traffic to their malicious IP address: Once the router has been rebooted, traffic from any device connected to that router can be rerouted. For example, a user trying to visit cnbc.com could unknowingly have their request rerouted to a malicious IP address. At this point, the WiFi hijacker will fetch cnbc.com’s web page infect and bundle it with malicious code before serving this compromised page to the user. This is commonly known as Man in the Middle attack.
When the modified page is retrieved by a user, that user can easily be targeted with injected ads. Although the user has not necessarily downloaded any malware, the use of a malicious proxy server makes them vulnerable to Customer Journey Hijacking and a variety of other online risks.
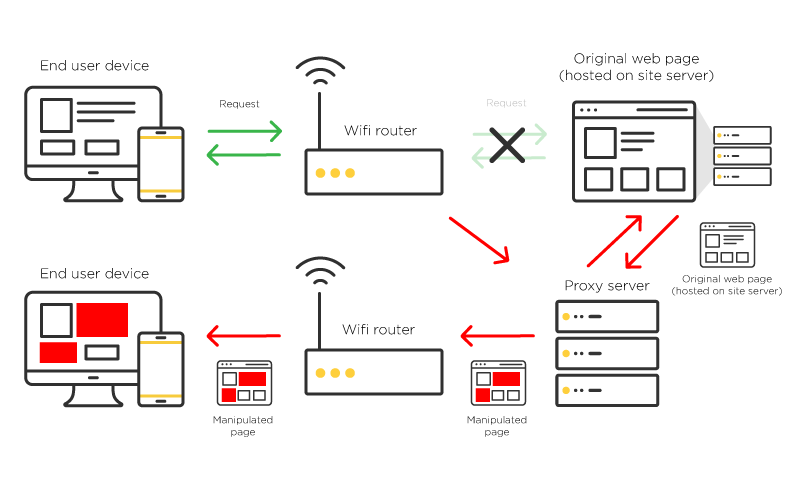
This type of process routinely hijacks WiFi users – whether at home, their local coffee shop, or an airport terminal – compromising their online journey, security, and privacy.
But what about network security measures like HTTPS? If a hacker already has control of a WiFi network, they also have control over all traffic going into or out of that network. One of the typical ways they work around HTTPS websites is by wrapping the original web page’s content within an iframe and adding malicious code all around that page.
This way, they can sidestep HTTPS connections in that network and continue to reroute traffic from users to malicious IPs.
How does WiFi-driven CJH jeopardize your online sales?
When hackers engage in Customer Journey Hijacking by leveraging WiFi connections, they expose shoppers to injected ads – just like in the more common, malware-driven method of CJH. Between these two methods of Customer Journey Hijacking, injected ads appear during 15-25% of online shopping sessions.
While most of these ads promote products sold by competing online stores, others focus on content such as adult websites and online gambling. By damaging brand reputations, CJH threatens not only short-term sales, but also long-term customer relationships. On average, these ads reduce conversion rates among affected users by 12%.
Whether injected ads are powered by malware or WiFi hijacking, conventional cybersecurity measures are incapable of stopping them. Because the ads are not part of your website, you cannot see them directly. And because you cannot control your customers’ WiFi connections (just like you cannot prevent malware from being installed on their digital devices), you cannot eliminate the causes of CJH entirely.
So what can you do to protect your online store from injected ads? Today, it is possible to automatically identify and block ads from appearing on users’ devices through the innovative use of artificial intelligence. At Namogoo, this approach consistently boosts online retailers’ overall conversion rates by 2-5%, resulting in an increase of 5-7% in revenue per visitor.
How is Customer Journey Hijacking hurting your sales? For a look at the injected ads that shoppers see while visiting your online store, you can get a free website analysis.


