At Namogoo, we believe that the best way to prove the value of our solution is to show it. With every prospective customer, we run a 30-day “Proof of Value” (POV) to prove that our technology is both easy to implement, and ROI positive.
The POV applies an A/B test to the visitor population in which Customer Journey Hijacking has been detected. Group A, the control group, are left to their own devices, while Namogoo blocks ad injections for group B. Throughout the 30 days, we measure the difference of several KPIs, including conversion, cart abandonment, and retention.
In every POV we run, two things will almost always happen:
- Visitor sessions in which hijacking is detected will outperform unaffected sessions for several KPIs, regardless of whether the ad injection is blocked or not.
- Visitor sessions in which Namogoo blocks ad injections, will further outperform sessions in which they are detected but not blocked. We consistently see an improvement of 15-25% for conversion rates, and 20-30% in checkout abandonment rate, in the recovered (blocked) population when compared to the monitored population of hijacked visitor sessions.
Surprised? A lot of our customers are because there is a tendency to reverse cause and effect. It’s not that hijacked visitors are more likely to convert; rather, people who are more likely to convert are more susceptible to being downloading software containing ad injections.
There are several reasons for this. Research1 has shown that ad injections are more likely to be delivered to a user’s device from online shopping sites and via online advertisements. Price-conscious visitors are more likely to visit multiple shopping sites and interact with multiple display ads. They may also be more inclined to install extensions that inject coupons, or to click on pop-up links to cheaper alternatives to the products they are viewing.
Unfortunately, many of these free extensions come at the cost of injections running on the user’s device.
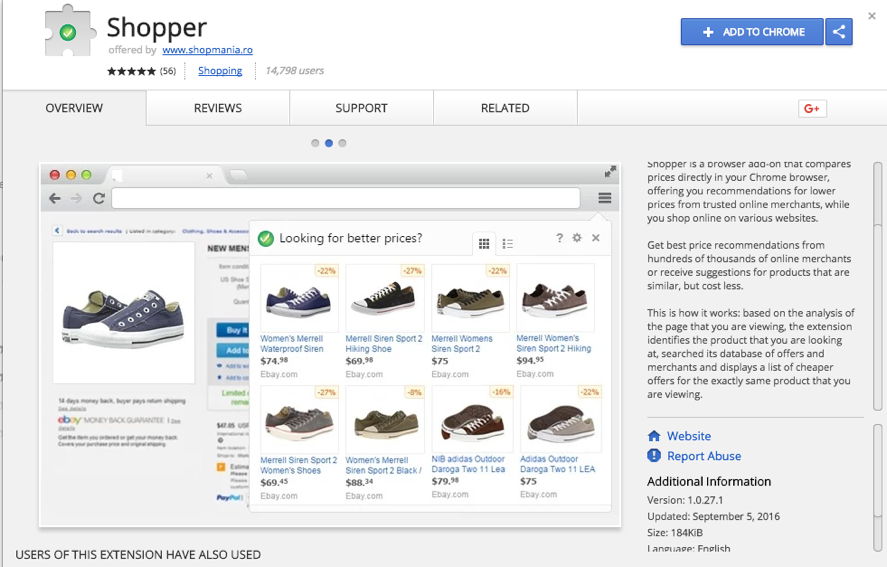 Many browser extensions offer ad injection as a service.
Many browser extensions offer ad injection as a service.
Even if the goals of the advertiser or extension developer are noble, they are very easily manipulated into unknowingly allowing ad injections to run through their code. Additionally, traffic hijackers will often attempt to buy popular extensions for this very purpose.2
With this knowledge in mind, the picture starts to become much clearer. A user clicks on an ad, or downloads an extension that installs ad injections on their device. The user browses your products, or places objects into the shopping cart and receives a popup, “buy this somewhere else, cheaper”. Your customer is now in someone else’s shop.
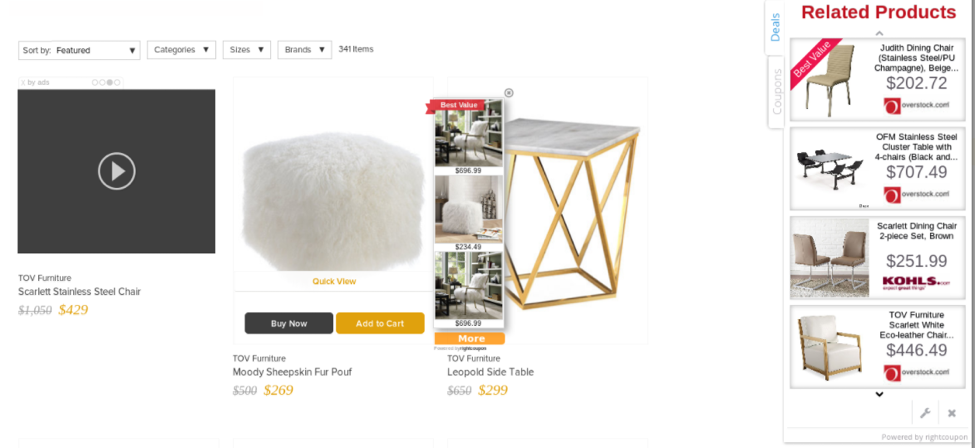 An example of injected advertising hijacking the intended customer journey.
An example of injected advertising hijacking the intended customer journey.
Unaddressed, a website runs the risk of having its most valuable customers, who are most likely to convert, lured away by offers of similar products available for cheaper, somewhere else.
By blocking such injections, Namogoo removes these unauthorized ads from your store. Users who are more likely to purchase are now free to browse your site with the intended user experience.
1https://www.cisco.com/web/offer/gist_ty2_asset/Cisco_2013_ASR.pdf
2https://adage.com/article/digital/big-ad-injection-scheme-hits-target-youtube-walmart/293088/



